Edition 4: Privacy Terrorism - Luigi Mangione's overlooked impact on corporate executives
TLDR: Luigi Mangione incited a less violent cohort, now committing Privacy Terrorism against executives. A hallmark example is LuigiWasRight[.]com which exposed the PII of 23,000+ executives in May. This doxxing increases the risk of cyber attacks and puts pressure on their Cyber Health.
Attack vectors: doxxing, account takeover, social engineering, spearphishing
The Murder: The assassination of CEO Brian Thompson marked a seminal moment for American corporations. A business person was murdered for professional reasons and the response from media and the public was mixed. The consensus response was outrage. Companies make tough decisions and mistakes, but violence is never appropriate, let alone murder. A loud minority was saying something new. Certain corporate executives deserve retribution, which can even include murder. Stunning mental gymnastics to arrive at an abhorrent justification. Nonetheless, security teams were forced to respond to this new sympathy.
The problem that was immediately budgeted for is physical security. Companies increased spend on bodyguards to protect their executives from physical harm. UnitedHealth reportedly hired bodyguards for 40 executives, after not having full time protection for even their CEO. Allied Universal, a private security company with 800,000 employees, claimed to field "hundreds of inquiries" in the days following Mr. Thompson's murder. Very few people are willing to die for their job. This is the type of risk that will cause companies to reopen budgets.
While the threat of violence was appropriately prioritized, Luigi Mangione inspired a new cohort of zealots. Not all of these zealots have murder in their veins, so they are exacting a different type of retribution. This ripple effect is emerging and will likely not receive the same level of press, but it poses a risk to corporate executives and board members.
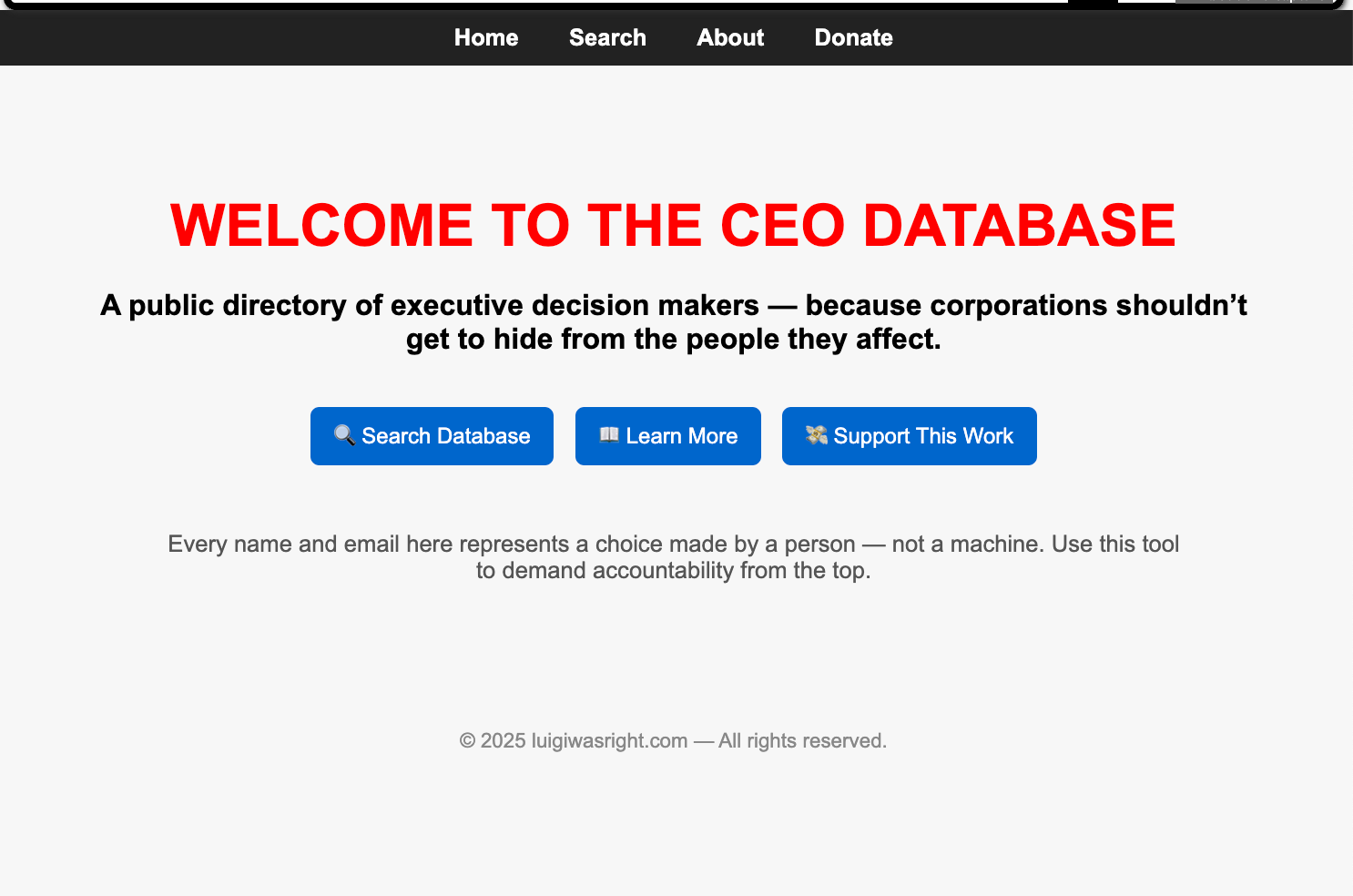
LuigiWasRight[.]com: 2 weeks ago, we uncovered a website called LuigiWasRight[.]com, an obvious nod to the perpetrator. The website shamelessly posted personally identifiable information of 23,000+ US executives. The PII included: First Name, Last Name, Email, Mobile Phone, Office Phone, Personal LinkedIn, Company Name, Job Title and Department. Collectively, these executives worked at 1,061 companies. There were other insurance companies like Geico and Farmers. But this site was beyond insurance and also featured well-known, publicly traded companies like 3M, Amazon, Apple, Boeing, Goldman Sachs, Raytheon, Starbucks and more. Below is a sample of impacted companies.

On its About page, the publisher explained that the "website is designed to empower ordinary citizens to reach decision makers directly." Poorly worded advocacy or a veiled threat, you can be the judge.
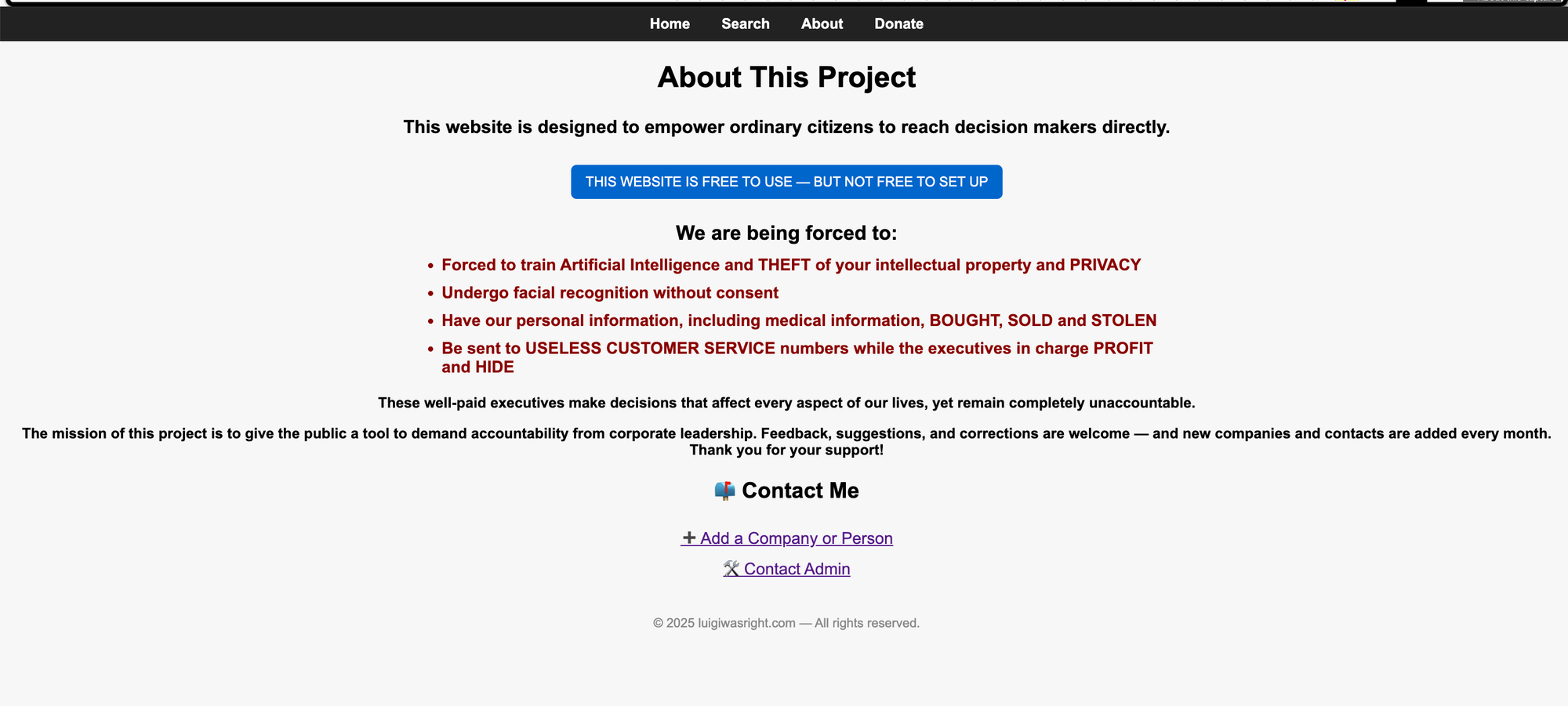
The underlying data was likely aggregated via open source intelligence (OSINT). Data brokers, data breaches and other freely available sources helped the publisher compile this PII. We also confirmed the data was fairly accurate (~70%.) with personal phone numbers being the most inaccurate. The site has since been taken down, we suspect by the registrar (Namecheap) or the hosting service. It briefly re-emerged in early June under the domain theceodatabase[.]com, but this too has since been removed.
Privacy Terrorism: We are predicting that LuigiWasRight[.]com is an archetype that executives will be increasingly exposed to. Under the guise of 'transparency' or 'accountability,' we expect doxxing, smear campaigns and meme-driven parodies to happen more frequently. Mangione inspired these non-violent but disruptive and invasive techniques and we're labeling it Privacy Terrorism. A working definition is: the malicious exploitation or exposure of private personal information with the intent to instill fear, manipulate behavior, cause reputational harm or exert coercive control.
Privacy Terrorism allows for performative social justice, a la Mangione, but does not incur the same risk for the perpetrator. Enforcement of cybercrime is generally more limited and lenient than that of physical crime. And with the latest budget cuts to our nation's cybersecurity infrastructure, prosecution and attribution are even less likely. Privacy Terrorism is 21st century occupational hazard.
How Privacy Terrorism Impacts Cybersecurity: These types of privacy violations "grease the wheels" for professional criminals and the mentally unstable, causing downstream risk for executives and board members. Certain cyber attacks become quite a bit easier once PII gets exposed. Here are some relevant cyber attacks our team is looking out for:
- Social media account takeover - when your personal email and social profile become exposed together, it puts a lot of pressure on your password, MFA and alert hygiene. If any of those are lacking, you are susceptible to a social media account being compromised. Hacking an executive's personal social media account in order to embarrass them happened to Rich Handler, CEO at Jeffries Group. His Instagram was compromised in 2021 and linked to a crypto-based fundraiser for Ukraine. Their stock was down 6% intraday on the news. There is also a belief that he gave a comment to a Financial Times story about the Instagram meme account Litquidity in order to suppress the Google search results about the hack.
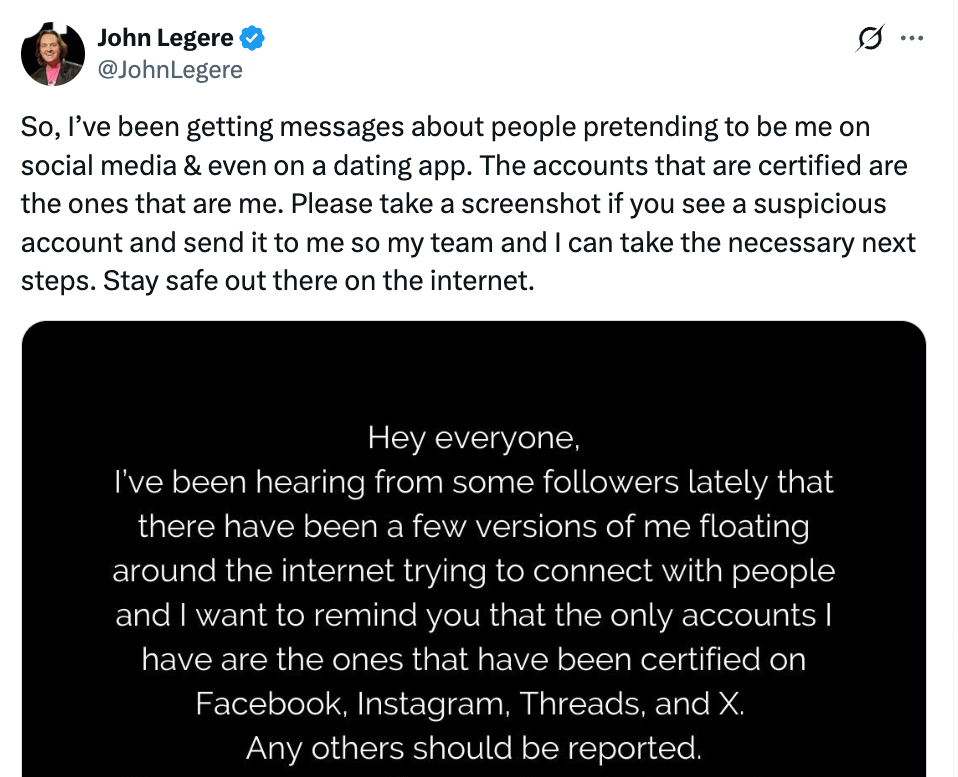
- Social media impersonation - the common impersonation case happens to executives who are active on social media, like John Legere, CEO at T-Mobile. He is flagrantly impersonated. The attacker then scams unsuspecting victims into phony investments. This "smash and grab" results in theft. These are typically 24-hour episodes and pose limited long term damage to the executive. The more vicious case is when the particular executive is not active on a platform. An attacker creates an account impersonating them and reaches out to actual friends and family. Depending on how long the deception lasts, the damage here can be severe.
- Subscription bombing - when your email becomes exposed, this is a common way to attack an executive. An attacker finds your email and then programmatically subscribes to hundreds of newsletters. Those confirmation emails overload your inbox and even your device. At its most basic level, it's a disruption prank. More maliciously, it can be combined with an account takeover attempt. The deluge of emails causes you to miss an important legitimate email such as "New Sign In Detected" or "Your Backup Email Has Been Changed." A critical account is compromised, all starting from a confirmed personal email.
- Swatting - should your home address become public, non-violent protests are a possibility. We have seen this with several of our executive Members. While those can be disruptive or even scary, they are nowhere near as dangerous as Swatting. A threat actor prank calls 911 in an attempt to dispatch a large number of armed police officers. Swatting has resulted in accidental death, as both the victim and police are understandably confused.
- Lateral attacks - when phone numbers or addresses become public, this can put a lot of pressure on people who share an address, like family. We worked with an executive whose family member was arrested. Once the child was linked to the executive by an address, the executive was extorted and harassed by opportunistic attackers who had a bone to pick with the executive's employer.
- Phishing - for highly skilled social engineers, a working, primary email address is all they need. When a website like LuigiWasRight[.]com tees up your position, employer, LinkedIn account and more, half the work is done for them.
How The Cyber Health Company Protects Our Members From This: You cannot minimize risk unless you measure it. As such, the first step in our Onboarding is conducting an OSINT report to map your discernible attack surface online. What can the author of the next LuigiWasRight[.]com find about you? We share that report to reveal what attackers can see about you and establish a baseline of risk.

From there, we offer a personalized Care Plan that includes shrinking your discernible attack surface. We remove certain online content (like removal from over 650 data brokers), tighten privacy settings for social media (like making your payments on Venmo private), and rotate credentials (especially those found on the dark web). We increase your digital hygiene/immunity. This means organizing credentials and ensuring they are current, email accounts are well maintained with tested recovery methods, software auto-updates and more. All of these measures make it easy to respond, in the event that there is a new threat. Ideally, we're executing your Care Plan prior to any Privacy Terrorism.
We also set up monitoring on your name so that we can alert you when there is a new exposure. If you are, unfortunately, targeted in something like LuigiWasRight[.]com, we immediately notify you in clear language. (We actually found the site because select Members were mentioned).
With your attack surface already mapped, our targeted remediation to Privacy Terrorism becomes much easier. Our team of experts is well positioned to deliver a targeted response. Moreover, by being previously organized, the response is more limited and more efficient to dispel any new risk. Not only do we measure you and educate you about your exposure, but we proactively minimize risk and save you time and privacy costs when it's time to respond.
Jeremy Banon
Founder/CEO
The Cyber Health Company
About The Cyber Health Journal: This journal analyzes a product, feature or recent development in technology and how it impacts personal cybersecurity, online privacy and digital immunity.
About the Author: Jeremy Banon was hacked in 2016 and founded The Cyber Health Company in 2021 to help others avoid the same fate. The company provides the toolkit and team to support the personal cybersecurity, online privacy and digital immunity of high-risk individuals and corporate executives.
