Edition 3: Coinbase's Compromise and How We Protect Against Insider Threat
TLDR: Bribed employees exposed PII of ~70k Coinbase customers. Social engineering attacks ensue, resulting in $100m+ of customer losses and counting. Read more for ways to limit your risk and how The Cyber Health Company protects against insider threat.
Attack vectors: social engineering, spearphishing, insider threat
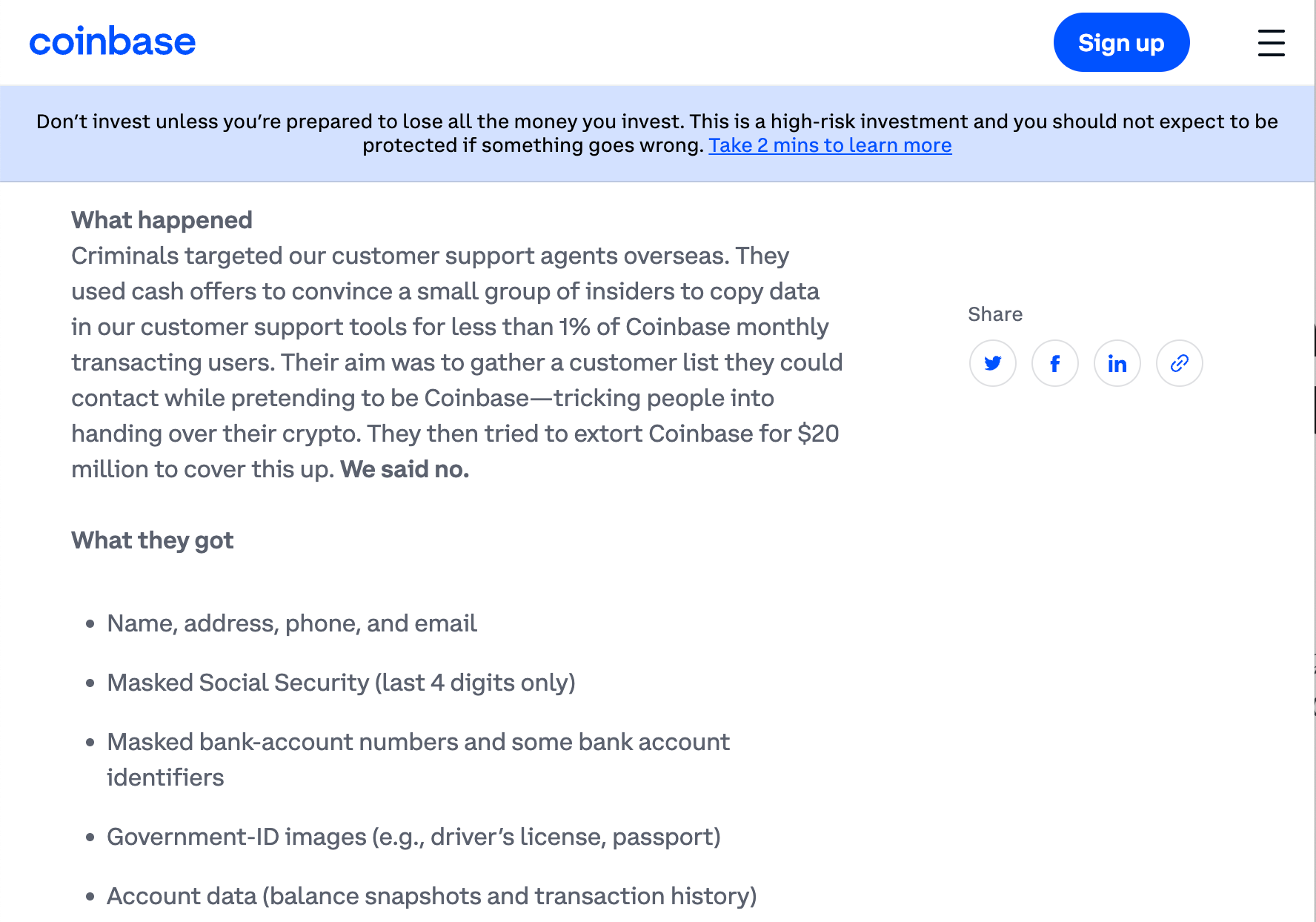
What happened: Coinbase acknowledged in a May 15th 8-K and a blog post that they were compromised via insider threat. Support agents, hired as contractors in India, were bribed by attackers to share customer PII. PII included: names, addresses, phone numbers, emails, last 4 digits of Social Security, masked bank‑account numbers, government‑ID images (e.g., driver’s license, passport), account balance and transaction history. The company claims the following was NOT exposed: login credentials, 2FA codes, private keys, any ability to move or access customer funds, access to any customer hot or cold wallets. High net worth clients are known to be affected, including Sequoia Capital Managing Partner, Roelof Botha.
Attackers have been actively leveraging the PII since December to conduct social engineering against unsuspecting customers. They impersonate Coinbase security to steal funds. So far, the most notable victim to come forward is Artist Ed Suman, who lost $2,000,000. As of 5/19/25, the DOJ is investigating the breach. This is a developing story.
How to assess if you were impacted: You received an email from no-reply@info.coinbase.com on 5/15 at 7:20am ET confirming your exposure to the breach.
If you were impacted and recently compromised: Coinbase is reportedly reimbursing stolen funds. Reach out immediately to security@coinbase.com to initiate your reimbursement.
If you were impacted and not recently compromised: For those in the preventative camp, the main Cyber Health risk is the active attack happening to others: stolen PII being used to impersonate Coinbase to extract funds. As the Coinbase blog emphasizes, “Expect imposters.” If you receive a call claiming you have a security event at Coinbase, hang up the phone. If you receive an email or text that your funds are at risk, do not engage.
The same is true for calls, texts or emails that purport to be from other companies. Never allow the citation of authentic PII, (which is now in the possession of criminals and should be considered public!) to encourage you to drop your guard. Remain vigilant. Do not be scared to hang up the phone, or disregard a text. As always, urgency is a red flag.
Outside of social engineering, the risks associated with this level of PII exposure are plentiful. Because physical IDs were exposed, identity-based attacks that leverage driver’s licenses or passports are expected. Locking your credit is always the advisable default state. Spearphishing attacks are also expected because name/email combos are exposed. See Journal Entry #2 on Phishing Concierge for further guidance on handling questionable emails.
Lastly, if you have a large balance that was exposed, consider working with us at The Cyber Health Company. A breach that publicizes your extractible value is a good catalyst to invest in your Cyber Health. Personal cybersecurity, online privacy and digital immunity are ultimately your responsibility. If companies like Coinbase are going to give contractors unfettered access to your SSN, they are not enough. At their best, they are product security. We are You security.
How The Cyber Health Company protects against insider threat: We custody information on high value targets. Outside of data security, how do we prevent bad apples from being a part of our team?
Background Checks - Before employing anyone, we conduct rigorous background checks using ex-FBI analysts, OSINT techniques and threat intelligence tools to look for signs of compromise. This also includes national security-based assessment to clear any future risk of sympathy to adversaries. Less than perfect candidates are rejected.
Employment Agreement - Every new hire must sign this. It states that if they abuse data privacy, we will terminate, claw back equity and aid law enforcement in their prosecution.
I will not… copy, capture, or disclose any information or screenshots from customer devices or otherwise access any customer’s device or any information thereon. I acknowledge and agree that any violation is subject to disciplinary action up to and including, to the extent permitted by applicable law, claw-back of equity, immediate termination, and other legal or disciplinary action by the Company, in its sole discretion, and to the fullest extent permitted by law. The Company reserves the right to report any violation of this Section 2 to law enforcement along with a request to prosecute such violation to the fullest extent of the law.
US Only - As a response to this compromise, Coinbase announced they are “opening a new support hub in the US” We have only hired US-based employees. Company hardware may not leave the country. This guarantees the strong justice system and the clause above are applicable. International extradition or employment laws are the concern of other companies. Domestic labor is a worthwhile security cost.
Jeremy Banon
Founder/CEO
The Cyber Health Company
PS: General Support appointments can always be booked for anything ad hoc, like advising on crypto custody. We do not custody assets on behalf of customers, but can advise on custody, backup and inheritance solutions.
About The Cyber Health Journal: This journal analyzes a product, feature or recent development in technology and how it impacts personal cybersecurity, online privacy and digital immunity.
About the Author: Jeremy Banon was hacked in 2016 and founded The Cyber Health Company in 2021 to help others avoid the same fate. The company provides the toolkit and team to support the personal cybersecurity, online privacy and digital immunity of high-risk individuals and corporate executives.
